Do you know how hard it is to install ClamAV as a service, together with Kerio Connect / Mailserver ? I do. Very annoying but since you don’t want to pay for the extra AV option within Kerio Connect / Mailserver, ClamAV could be a nice option. But how. Well, it’s a mix of a bundle of tools. Let me get you started. NOTE: this is NOT the perfect way to install, but it worked for me so YMMV.
1. Install ClamWin Free Antivirus (this doesn’t install the service but it’s an easy way to get the database updates…). Use this path when installing: C:\ClamAV.
2. Download ClamAV for Windows and extract it to C:\ClamAV
3. Create these extra folders:
C:\ClamAV\tmp
C:\ClamAV\db
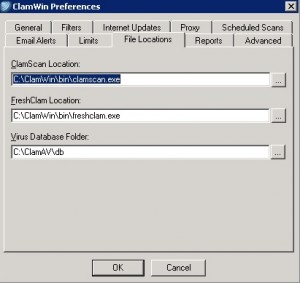
4. Modify the Antivirus Database download folder in ClamWin Free Antivirus to point it to C:\ClamAV\db and update the DB.
5. Paste the Kerio Connect / Mailserver ClamAV config to C:\ClamAV\clamd.conf
PidFile C:\ClamAV\clamd.pid
LogFile C:\ClamAV\clamd.log
DatabaseDirectory C:\ClamAV\db
TemporaryDirectory C:\ClamAV\tmp
TCPSocket 3310
TCPAddr 127.0.0.1
DetectPUA yes
DetectBrokenExecutables yes
HeuristicScanPrecedence yes
ArchiveBlockEncrypted yes
StreamMaxLength 30M
6. Now for the tricky part: running clamd.exe as a service (clamd.exe –install didn’t work for me). You’ll need the Windows Resource kit for your server; mine is a Windows 2003 box. Get it here : Windows Server 2003 Resource Kit Tools and copy / move instsrv.exe and srvany.exe in the same directory of ClamAV (C:\ClamAV).
6. Goto DOS prompt (cmd) and go to C:\ClamAV. Enter:
instsrv.exe clamD c:\ClamAV\srvany.exe
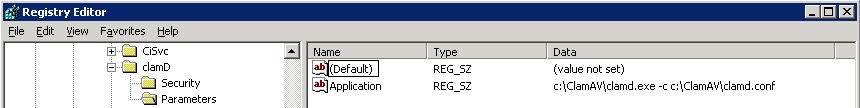
7. Now edit the registry to let clamd.exe run using it’s clamd.conf file when started as a service.
NOTE: It is dangerous to edit the registry, follow carefully
- Navigate to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\clamD
- Right click on clamd and create a new Key called Parameters
- Right click on Parameters and create a new String Value called Application
- Edit the new Application REG_SZ and add c:\ClamAV\clamd.exe -c c:\ClamAV\clamd.conf
8. Then you can start and stop clamD in Services or manually:
net start clamD
You can check if clamav is listening at the right port:
netstat -a | findstr 3310
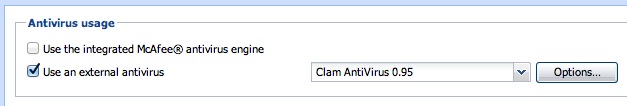
9. Time to tell Kerio Connect / Mailserver that we have a running ClamAV daemon, ready to answer all AV questions:
- Open the Kerio Connect’s Administration
- Go to Configuration->Content Filter->Antivirus
- Enable option “Use external antivirus†(near the top)
- Choose “Clam Antivirus”
- Click “Apply” (near the bottom) to save settings
And that’s it !