As a default, Sophos / Astaro UTM’s SMTP Proxy listens on all external IP addresses. Quite annoying if you have an internal mail server that you want to let your external users use for sending (authenticated) emails, since UTM will intercept all SMTP traffic.
Here’s how I solved that (only works if you have at least 2 public IP addresses).
– NAT one external public IP address to your internal mail server (so forward at least ports 25, 465, 587; use the IP address that you use for (example) mail.yourdomain.com. In this example I use 23.37.149.232 (WAN – FW2)
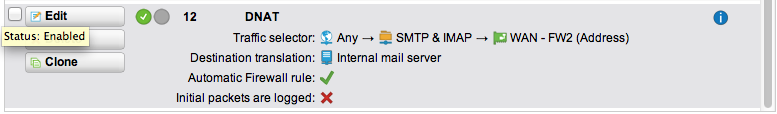
– enable SMTP proxy on your UTM (your UTM will now listen on all your external public IP addresses)
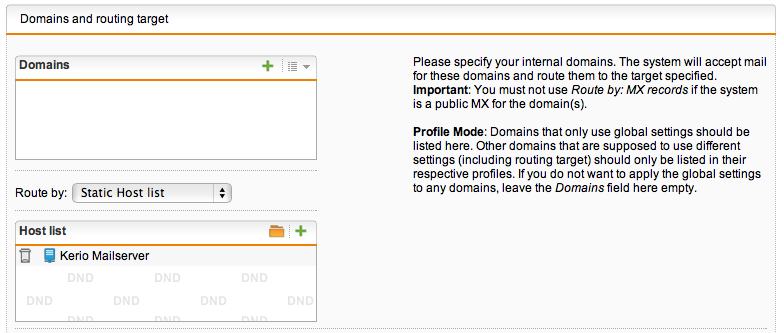
– configure SMTP routing to forward MX emails to your internal server
– SSH to your UTM and become root
– with vi, edit this file:Â /var/storage/chroot-smtp/etc/exim.conf
– edit this line, remove the # and enter your public IP address to reflect your MX record (like mx.yourdomain.com):
local_interfaces = 23.37.149.233:81.37.153.126:59.94.132.164
(I have 3 SDSL lines on my Sophos UTM box, separate each entry with semicolons)
– restart your EXIM service:
/var/mdw/scripts/smtp restart
Check you SMTP Proxy log file, something like this should appear:
listening for SMTP on [23.37.149.233]:25 [23.37.149.233]:587 [81.37.153.126]:25 [81.37.153.126]:587 [59.94.132.164]:25 [59.94.132.164:587]
Done. Now, Sophos UTM will intercept your incoming MX traffic (and if setup right, forward non-junk emails to your internal mail server) while the other IP address is useable for your users as an authenticated relay-server. 23.37.149.232 is used directly by the mail server, 23.37.149.233, 81.37.153.126 and 59.94.132.164 by Sophos as incoming MX server.
