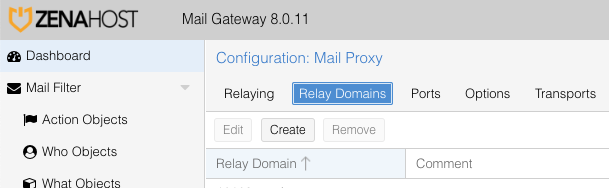
After you successfully imported all Hestia mail domains into your Proxmox Mail Gateway, you might want to sync Hestia to PMG when you add OR delete a mail domain in Hestia as an allowed Relay Domain mail destination on your Proxmox Mail Gateway. Here’s the how-to!
Make sure your Hestia server can establish a trusted SSH connection to the PMG server, using private keys. You can find plenty of guides on how to do so.
On the Hestia server, create the hooks folder and the add domain script:
mkdir /usr/local/hestia/data/hooks/ cd /usr/local/hestia/data/hooks/
vi v-add-mail-domain-after
Enter:
#!/bin/bash ssh pmg pmgsh create /config/domains --domain "$2" --comment "$1_`date "+%Y-%m-%d"`"
Save and exit vi. This will connect to your PMG server and create the mail domain with the username and creation date in the comment.
Create the delete domain script:
vi v-delete-mail-domain-after
Enter:
#!/bin/bash ssh pmg pmgsh delete /config/domains/$1
Save and exit vi. This will execute the command and delete the mail domain on the PMG server.
Make the scripts executable:
chmod +x *
Now you need to modify the v-add-mail-domain and v-delete-mail-domain Hestia scripts to execute the hooks.
vi /usr/local/hestia/bin/v-add-mail-domain-after
At the end of the file, before the exit entry, add this:
# Adding new domain to Proxmox Proxy List /usr/local/hestia/data/hooks/v-add-mail-domain-after $user $domain $BIN/v-log-action "$user" "Info" "Mail" "Mail relay entry on Proxmox added (Domain: $domain)."
Save and exit vi. This will execute the previously created hook and adds an entry into the user’s log file.

Now for the v-delete-mail-domain command:
vi /usr/local/hestia/bin/v-delete-mail-domain-after
At the end of the file, before the exit entry, add this:
# Delete mail domain from Proxmox Proxy list sh /usr/local/hestia/data/hooks/v-delete-mail-domain-after $domain $BIN/v-log-action "$user" "Info" "Mail" "Mail relay entry on Proxmox deleted (Domain: $domain)."
Save and exit vi.
That’s it! Now add your new mail domain and it’ll show up on your Proxmox Mail Gateway. Or delete it 🙂